The Authenticity of Catfish: A Critical Look
https://showfakes.com/wp-content/uploads/2023/12/1200px-Catfish_the_TV_Show_Logo-1024x497.png 1024 497 Admin Admin https://secure.gravatar.com/avatar/9c89a0590fb34eb4e2bf2f9088e9f86a?s=96&d=mm&r=gIntroduction:
In the vast and interconnected world of the internet, where social interactions transcend geographical boundaries, the phenomenon of catfishing has become a prevalent concern. Catfishing refers to the act of creating a fake online persona to deceive others, typically for personal, emotional, or financial gain. The term gained popularity through the documentary and subsequent television series, “Catfish,” where filmmakers explored the complexities of online relationships and the deceptive nature of some individuals.
Defining Catfishing:

Catfishing involves the creation of a false identity, often with the intent to establish a relationship with someone who is unaware of the deception. The motivations behind catfishing can vary widely, ranging from seeking emotional validation to financial scams. The term itself originates from the world of fishing, where catfish are known to chase prey into tight spots, analogous to how a catfisher lures their victims into a web of deceit.
The Evolution of Catfishing:
As technology has advanced, so too have the methods of catfishing. While the classic image of a catfisher might involve a fabricated online dating profile, modern catfishing extends to various platforms, including social media, gaming communities, and even professional networking sites. The anonymity afforded by the internet makes it easier for individuals to create alternate identities and manipulate unsuspecting victims.
Common Catfishing Scenarios:
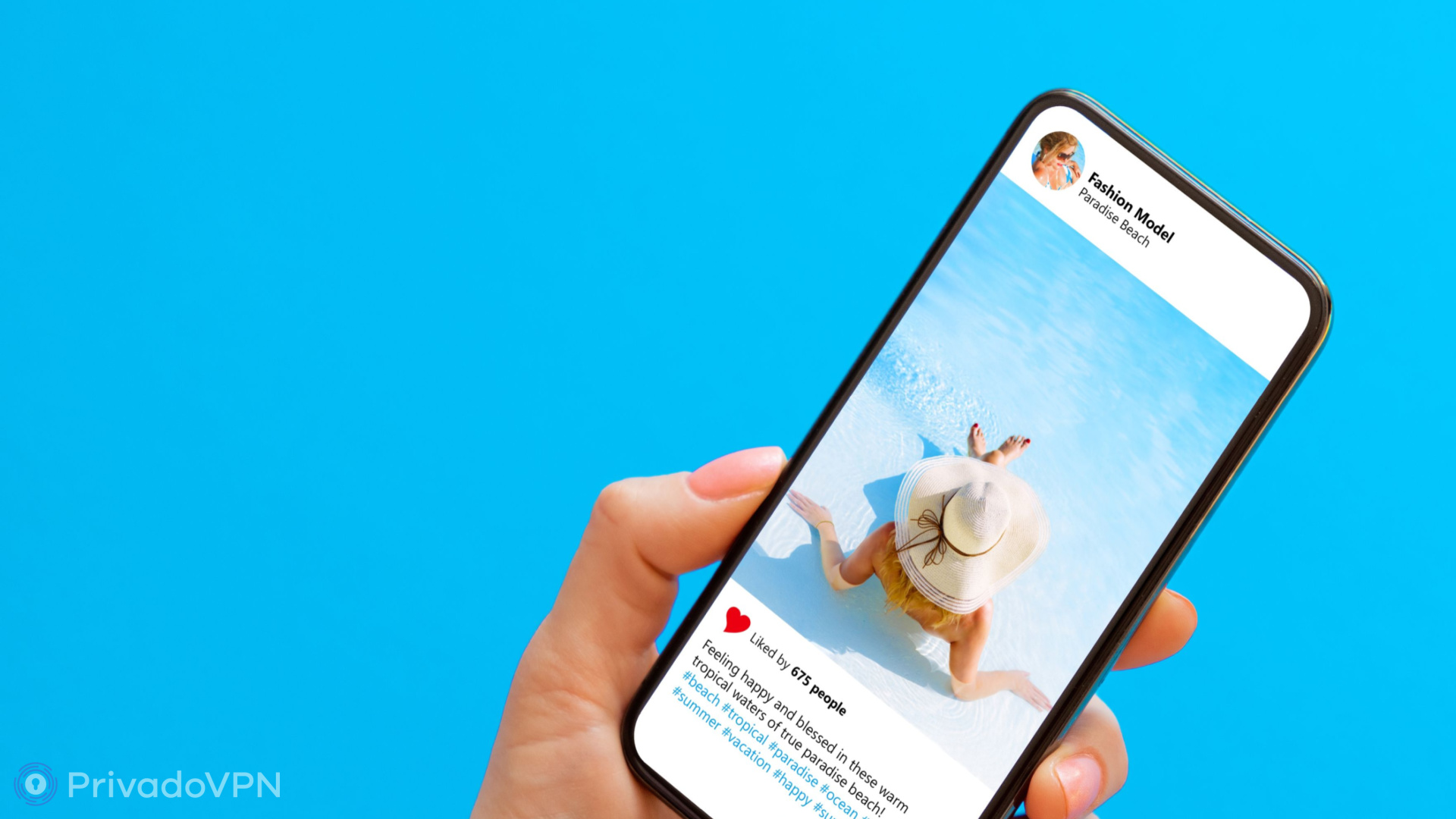
- Romantic Relationships: Catfishers often target individuals seeking romantic connections. They may use fake profiles and stolen photographs to create an attractive persona, luring the victim into a relationship based on emotional connection and trust.
- Financial Scams: Some catfishers exploit their victims for financial gain. They may invent elaborate stories to evoke sympathy, convincing the target to send money or share sensitive financial information.
- Social Engineering: Catfishing extends beyond personal relationships to infiltrate social circles and online communities. The catfisher might exploit trust within a group, causing discord or manipulating events for personal amusement or gain.
The Psychology of Catfishing:
Understanding the psychology behind catfishing is crucial to addressing this phenomenon. Various factors contribute to an individual’s decision to engage in catfishing, including loneliness, low self-esteem, a desire for attention, or even a misguided sense of revenge. In some cases, catfishers may have experienced trauma, leading them to seek solace in the creation of an alternate persona.
Spotting a Catfish:

While catfishers can be cunning, there are common signs that may indicate a potential catfishing scenario. These include:
- Unrealistic Photos: Catfishers often use images of attractive individuals found online. A reverse image search can help verify the authenticity of the photos.
- Inconsistencies in Stories: Catfishers may struggle to maintain consistent narratives about their lives. Paying attention to inconsistencies in their stories can unveil deception.
- Reluctance to Meet in Person: A classic sign of catfishing is the reluctance or refusal to meet in person. Catfishers often create excuses to avoid face-to-face interactions.
- Request for Money: Catfishers may attempt to exploit their victims financially. Any request for money or financial assistance should be met with skepticism.
Motives and Masks
At the heart of every catfish lies a desire, but it’s not always romantic. Some catfish seek validation and attention, crafting online personas that garner likes, shares, and a sense of belonging. Others engage in a twisted form of escapism, shedding their real-life identities for the thrill of inhabiting someone else’s. And then there are the predators, those who exploit the vulnerability of lonely hearts or use deception for financial gain. Understanding these diverse motivations is crucial to recognizing the warning signs and protecting oneself from harm.
Conclusion:
The world of online interactions is both vast and diverse, offering opportunities for meaningful connections but also posing risks of deception. Catfishing, while prevalent, can be mitigated through awareness, education, and vigilant online behavior. Recognizing the signs of catfishing is essential for individuals navigating the digital landscape, fostering a safer and more authentic online experience for all.